Data Scientists Must Focus on Data Security Risk

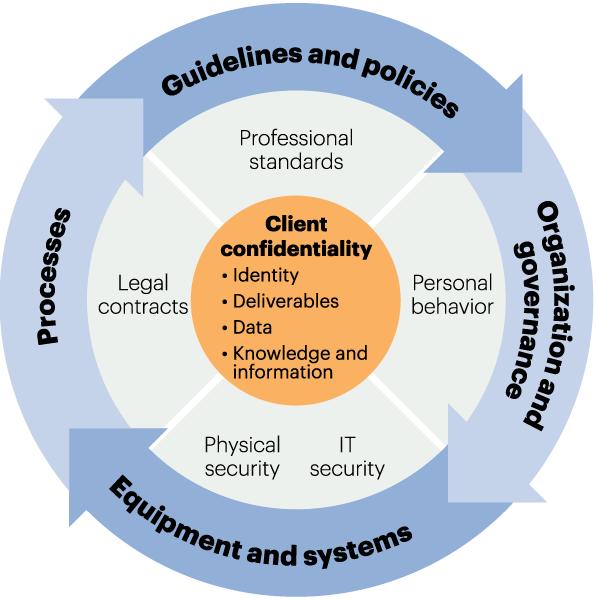
Last week we discussed the importance of data scientists prioritizing client confidentiality and the concern of exposing high-value information to (internal or external) data scientists who may share this information with competitors.
In addition, many organizations are reluctant to build modern data analytical ecosystems because of real and perceived data security concerns.
While there are current database security solutions such as Accumulo and private hybrid cloud designs with modern security systems to mitigate potential hacks and protect valuable information, many organizations do not fully understand how vulnerable their current data systems are and do not appropriately analyze the significant risks of a data breach.
The solution is architecting and building a modern data analytical ecosystem with robust data security and designing and executing an information management strategy and knowledge processes to protect high-value information.
The Cyber Risk Report 2015 outlines critical security issues that all organizations must prioritize. Key findings include:
Well-known attacks are still commonplace: Attackers continue to leverage well-known techniques to successfully compromise systems and networks. Many vulnerabilities exploited in 2014 took advantage of code written many years back; some are even decades old. Adversaries continue to leverage these classic avenues for attack.
Misconfigurations are still a problem: The 2013 report documented that a large percentage of vulnerabilities reported were related to server misconfiguration. The trend continued in 2014, with misconfigurations being the number-one issue across all analyzed applications. Our findings show access to unnecessary files and directories dominates the list of misconfiguration-related issues.
Newer technologies introduce new avenues of attack: As new technologies are introduced into the computing ecosystem, they bring with them new attack surfaces and security challenges. This past year saw a rise in already prevalent mobile-malware levels. Even though the first malware for mobile devices was discovered a decade ago, 2014 was the year in which mobile malware stopped being considered just a novelty. Connecting existing technologies to the Internet also bring a new set of exposures. Point-of-sale (PoS) systems were a primary target of multiple pieces of malware in 2014. As physical devices become connected through the Internet of Things (IoT) - a paradigm that brings ubiquitous computing and its security implications closer to the average person.
Determined adversaries are proliferating: Attackers use both old and new vulnerabilities to penetrate all traditional levels of defenses. They maintain access to victim systems by choosing attack tools that will not show on the radar of antimalware and other defense technologies. In some cases, these attacks are perpetrated by actors representing nation-states, or are at least launched in support of nation-states. Network defenders should understand how events on the global stage impact the risk to systems and networks.
Cyber-security legislation is on the horizon: Activity in European and US courts linked information security and data privacy more closely than ever. As legislative and regulatory bodies consider how to raise the general level of security in the public and private spheres, there was an avalanche of reported retail breaches in 2014. This spurred increased concern over how individuals and corporations are affected once private data is exfiltrated and misused. Companies should be aware that new legislation and regulation will affect how they monitor their assets and report on potential incidents.
Secure coding continues to pose challenges: The primary causes of commonly exploited software vulnerabilities are consistently defects, bugs, and logic flaws. Cyber security research professionals have discovered that most vulnerabilities stem from a relatively small number of common software programming errors. While much has been written on how to integrate best secure-coding practices into their daily development work, we continue to see old and new vulnerabilities in software.
Complementary protection technologies fill out coverage: In May 2014, a senior executive of a prominent anti-malware vendor declared antivirus dead. The industry responded with a resounding “no, it is not.” Both are right. Studies show that antimalware software catches only about half of all cyberattacks—a truly abysmal rate. In our review of the 2014 threat landscape, we find that enterprises most successful in securing their environment employ multiple layers of complementary protection technologies. These technologies work best when paired network policies and practices that assume a breach will occur, instead of one that only aims to prevent intrusions and compromise. By using all tools available and not relying on a single product or service, defenders place themselves in a better position to prevent, detect, and recover from attacks.
